The ARPANET pioneered the creation of novel encryption devices for packet networks in the 1970s and 1980s, and as such were ancestors to today's IPsec architecture, and High Assurance Internet Protocol Encryptor (HAIPE) devices more specifically.
DuPont and Fidler provide a historical perspective of ARPANET encryption devices in the broader evolution of computer networks and cybersecurity. [1] They focus primarily on the first such ARPANET device, the Private Line Interface (PLI). That said, the PLI was just the first in a series of devices created during the 1970s and 1980s in ARPANET-related research and development: [2]
- Private Line Interface (PLI)
- Black-Crypto-Red (BCR)
- Blacker
- Internet Private Line Interface (IPLI)
Private Line Interface (PLI)
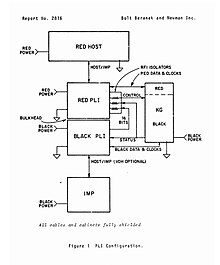
The Private Line Interface (PLI) was the first packet encryptor, sponsored by the Advanced Research Projects Agency and implemented by BBN Technologies as part of the creation of the ARPANET. It was in an early ideation phase by 1973, [3] with a stated goal of providing users with the equivalent of a private, leased line through the ARPANET. In that early phase, the PLI was envisioned to provide two distinct capabilities: transferring a continuous bit steam over the ARPANET, and possibly encrypting the bit stream while it was within the ARPANET.
As design progressed, it evolved into a packet encryption device, which was approved starting in 1975 by the National Security Agency for limited deployment on the ARPANET, to protect classified data as it passed through the network. [2] Each PLI device incorporated a KG-34 encryption device, and as a result was a manually keyed system. [4]
Black-Crypto-Red (BCR)
Black-Crypto-Red (BCR) was an experimental, end-to-end, network packet encryption system developed in a working prototype form by BBN and the Collins Radio division of Rockwell between 1975 and 1980. BCR was the first network security system to support TCP/IP traffic for IPv3, and it incorporated the first Data Encryption Standard (DES) chips that were validated by the U.S. National Bureau of Standards (now called NIST). [5] It provided automated, KDC-based key management and access control (as later adopted by Kerberos and Blacker), [2] and supported IP header bypass. [6]
Blacker
The first Blacker program began in the late 1970s, with a follow-on eventually producing fielded devices in the late 1980s. [7] It was sponsored by the National Security Agency as a very high assurance (A1), multi-level security system, and developed by SDC (software) and Burroughs (hardware), and after their merger, by the resultant company Unisys. [2]
Internet Private Line Interface (IPLI)
The Internet Private Line Interface (IPLI) was created by BBN as a successor to the PLI. It was updated to use TCP/IP (IPv4) and newer COMSEC technology ( KG-84), but still manually keyed. [2] They were intended for use in the Defense Data Network and also in DARPA Low-Cost Packet Radios in the SURAN project.
References
- ^ "Edge Cryptography and the Codevelopment of Computer Networks and Cybersecurity", by Quinn DuPont, Bradley Fidler, IEEE Annals of Computing, vol. 38, Oct.-Dec. 2016, pages 55-73.
- ^ a b c d e "Re: Network Layer Encryption History and Prior Art", email by Steve Kent on the ipsec mailing list, Wed, 19 Jun 1996 10:59:39 +0100
- ^ "Interface Messages Processors for the ARPA Network", Quarterly Technical Report No. 2, by Frank E. Heart, BBN Report 2580, BBN Technologies, pages 10-13.
- ^ "Interface a Private Line Interface (PLI) to an IMP and a Host to a PLI", in Specifications for the Interconnection of a Host and an IMP, BBN Report No. 1822, Appendix H, January 1976.
- ^ Internet Security Glossary, Version 2, RFC 4949, August 2007.
- ^ Trust in Cyberspace, National Academies Press, 1999, page 301.
- ^ DARPA Technical Accomplishments: An Historical Review of DARPA Projects, vol. 1, by Sidney G. Reed, Richard H. Van Atta, and Seymore J. Deitchman, IDA Paper P-2192, 1990, pages 20-18 to 20-20.